In yet another significant security breach, unknown malicious agents targeted Ledger, the popular hardware wallet provider, aiming to exploit their LedgerConnect kit. Blockaid, a platform aiming to protect web3 users, was the first to report on the attack.
The Supply Chain Attack Targeting Ledger Connector
Taking to X on December 14, Blockaid said attackers successfully injected a “wallet-draining payload” into the NPM package. Once the payload propagated, attackers hijacked the front end of multiple apps, including Sushi, Hey, and Zapper, crippling operations and reportedly making away with hundreds of thousands of dollars worth of assets.
The attack wasn’t targeting any dapp or blockchain like Solana or Ethereum, for example. Instead, hackers wanted to exploit all protocols whose users, in one way or another, used the LedgerConnect kit to manage or transfer assets.
To understand how the hack was executed, hackers expressly targeted Ledger’s NPM. The connector is crucial in how typically off-chain Ledger wallet clients can securely connect and manage their assets online.
While providing a means of accessing wallets, NPM is also an interface. Through this portal, developers can integrate Ledger hardware wallets into apps. In this case, Ledger users can securely engage in non-fungible tokens (NFTs), decentralized finance (DeFi), and other activities.
Since this attack aimed to exploit a critical Ledger infrastructure that could impact all protocols regardless of blockchain, analysts now say these agents successfully executed a “supply chain attack.” In supply chain attacks on DeFi protocols, hackers can target a trusted service provider, mostly a wallet provider or exchange, to steal funds.
Ledger Responds, Over $480,000 Stolen
Wintermute’s Head of Research, Igor Igamberdiev, reported that a script infected with malware was uploaded to Ledger’s NPM register at 9:44 am UTC. However, Ledger has since responded, saying they deleted the malicious file and replaced it with a genuine version roughly four hours after the script was uploaded at around 1:35 pm UTC.
Ledger has also reminded users to be keen before signing off on their transactions, emphasizing that all addresses and information displayed on their interface are the “only reliable sources of information.” Earlier, the hardware manufacturer assured clients that their devices were not compromised.
Despite these assurances, Lookonchain, a blockchain analytics platform, said over $480,000 worth of assets were stolen before Ledger patched the error.
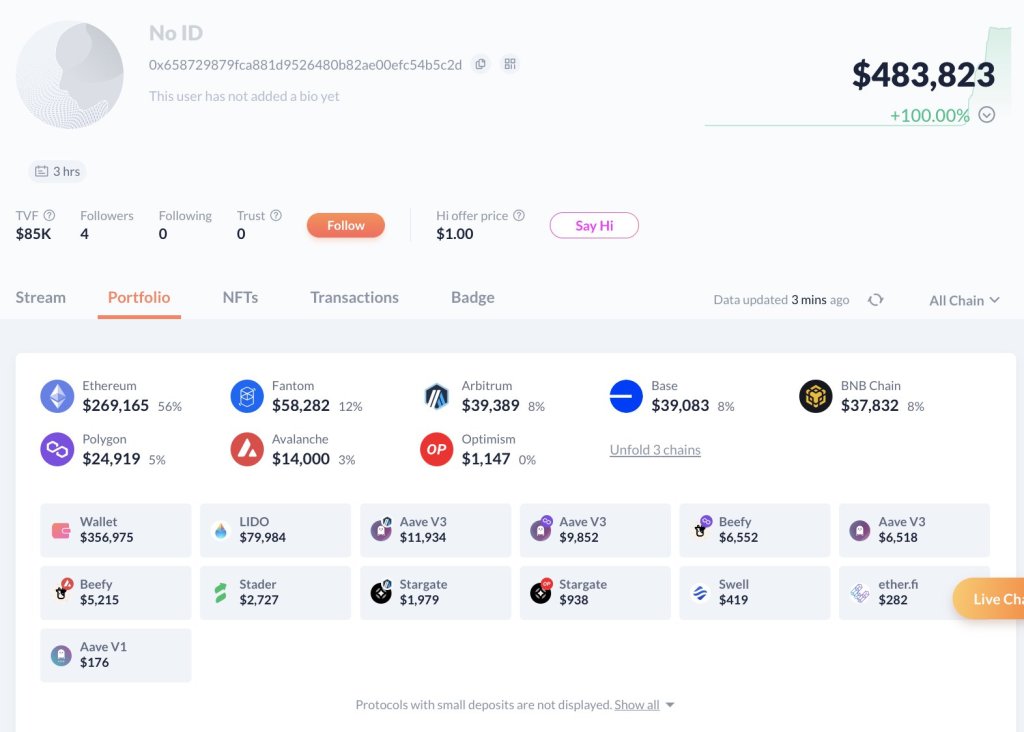
To further reinforce ZachXBT’s statement, Paolo Ardoino, the CEO of Tether, the USDT issuer, took to X, saying the platform had blocked the Ledger Exploiter’s address.

You can get bonuses upto $100 FREE BONUS when you:
💰 Install these recommended apps:
💲 SocialGood - 100% Crypto Back on Everyday Shopping
💲 xPortal - The DeFi For The Next Billion
💲 CryptoTab Browser - Lightweight, fast, and ready to mine!
💰 Register on these recommended exchanges:
🟡 Binance🟡 Bitfinex🟡 Bitmart🟡 Bittrex🟡 Bitget
🟡 CoinEx🟡 Crypto.com🟡 Gate.io🟡 Huobi🟡 Kucoin.
















Comments